Httpsession Serialization
This article will guide through the process of implementing JWT authentication with Spring Boot. RELEASE/en/_images/session-management_overview_invalidate2.png' alt='Httpsession Serialization' title='Httpsession Serialization' />Top 50 Design Patterns Interview Questions and Answers. Indepth guide with answers to wow the interviewer. Bonus 20 Videos PDF interview guide. IBM WebSphere Application Server provides periodic fixes for the base and Network Deployment editions of release V8. The following is a complete listing of fixes. Introducing Thymeleaf 1. What is Thymeleaf Thymeleaf is a modern serverside Java template engine for both web and standalone environments, capable of processing. ZCbmAflOsUS6JblkcZh5ARKQNUqMiPky0L6bvVFeHYWuy5k7hzDabyRd39Vast9YjBMDnF-vsnbdwKHGGJQmemIQviXk6qckFAq4pPxGF29UazFUo9F2AD7sqtxkNtYxo7oONJxnYL8ul3iOU1VKYdoWNPPTuSEuZj66SjnWcBEfrzuUdgL09cLjjGmQ1TxHxZ5XM3O9N6SCXuqSsEfZw6zKFaKf9Kz69lfC2_JKUb6uvXtetzx3CvifP4Nj2nD5djwDT0FRyT05LASAEjKfCdBReaqGuAbzYNcXje9rDR_jc1SbZLcsiw_11L-DlOxK7RfVX6WVIMaMCPiEtq5XwHJZBg07yGAhcOQI9quokA-ekd34lD4PNX7_QLOabWqkXGkMUxsBKBv1vB2iQ3SZ7oSlC0v0JBKF4g=w1200-h630-p-k-no-nu' alt='Httpsession Serialization' title='Httpsession Serialization' />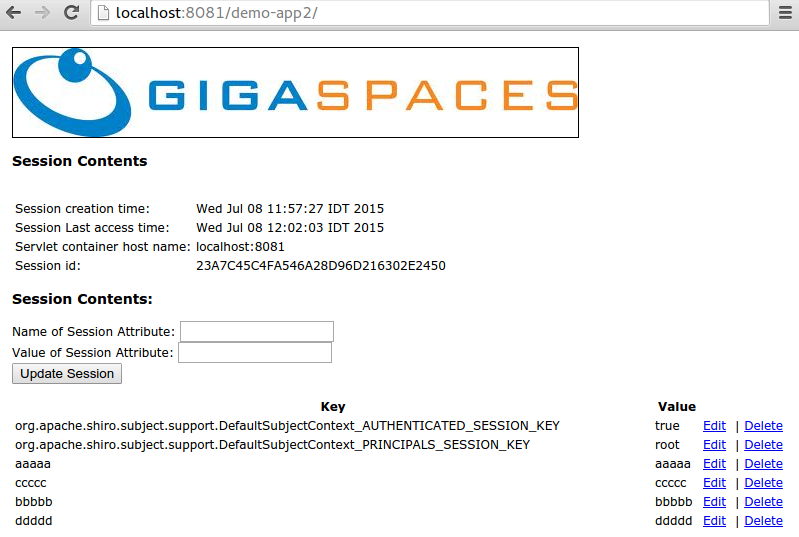 In this post, we will build a fullblown Spring MVC application secured using Spring Security, integrating with MySQL database using Hibernate, handling ManytoMany. KITmFjS0o/TV03bx1sNdI/AAAAAAAABfc/tNbDK2qSDrw/w1200-h630-p-k-no-nu/portletsessioninspection.JPG' alt='Httpsession Serialization' title='Httpsession Serialization' />
In this post, we will build a fullblown Spring MVC application secured using Spring Security, integrating with MySQL database using Hibernate, handling ManytoMany. KITmFjS0o/TV03bx1sNdI/AAAAAAAABfc/tNbDK2qSDrw/w1200-h630-p-k-no-nu/portletsessioninspection.JPG' alt='Httpsession Serialization' title='Httpsession Serialization' /> Gateway protection against Cross Site Request Forgery attacks. Gateway REST services open up the SAP landscape for consumption and operation from clients outside that trusted SAP landscape, including those evil browsers. Evil as we all know, the web cannot be trusted. A critical aspect in the Gateway architecture is therefore to mitigate the impact of web based security attacks. Cross Site Request Forgery CSRFOne of the most exploited security vulnerabilities on the web is cross site request forgery. The essence of a CSRF attack is that a malicious site misleads a trusting site in believing that a transactional request comes with approval of the user. The working of a CSRF attack is as follows 1 after the user has set up an authenticated session with an application site, 2 the user while still within this authenticated browser session visits a malicious site, and 3 the malicious site tricks the user in sending requests to the application site that are actually constructed by the malicious site. Misleading the trusting site that the request comes with approval from the authenticated and authorized user, while in fact it originates from a malicious site. Hence the name cross site request forgery. The success of CSRF attacks depends on 3 factors The ability to load malicious javascript code within the authenticated browser session. The ability to misuse the user authentication to the application site. In most browserwebapplications scenarios the users authentication state is maintained in cookies after successful authentication required to preserve the authenticated state. If the malicious site can lure the user into sending a malicious request from the authenticated browser session, that request will automatically include all cookies including the authentication state. And thus be authorized to the trusting site without the user being aware nor approved the request. The predictability of the transaction request, so that the malicious site is able to automatically construct a request that will be serviced by the trusting site. The first factor is common exploited by social engineering. The user is somehow seduced to load javascript code from the malicious site into the current browser session, without the user even be aware. Typical example is to send an email to user with hidden javascript code, and when the user opens it a request is send to malicious site. The protection against this risk are a combination of tooling mail filters and educating the users do not just open any received mail. Although the quality of both security measures increases yes, users are also more and more aware of the risks on the web, this protection is certainly yet not 1. Note that this factor is only present if the consumption of the webservices is via a browser. In case of a native application, and also in case of an embedded browser in native App e. Fiori Client, Kapsel, Cordova, the user cannot visit others sites and have its client context become infected compromised. The second factor is inherent present in all browsers. Without it, each request send from browser would first need to go through the authentication protocol with the remote webapplication, involving browser redirects, identity stores. And in case of usernamepassword browser logon, the user would have to reenter hisher credentials over and over again. Thus preserving the authentication state after initial authentication is needed to avoid the processing and elapse time for the authentication protocol handling, and to prevent unhappy users. User friendliness and security are often in contradiction. Protection against CSRF attacks CSRF Token. CSRF protection focusses on the 3rd factor make sure the request cannot be automically predicted and thus constructed. Introduce CSRF Token protection. Blackberry Os 10 Download For Playbook Bar more. The essence of CSRF Token protection is that the token is a secret key that is only known to the authenticated browser session and the trusting site, and that the authenticated browser session must include in each modifying request to the trusting site in order to convince the trusting site that the request is coming with consent from the user. CSRF token protection is utilized on modern webapplication platforms, including SAP ICF, Microsoft IIS, CSRF protection applied in Gateway. SAP Gateway applies the following protocol to protect against CSRF The user opens in browser a session with the Gateway based webapplication, and must first authenticate. This can be via any of the authentication methods usernamepassword, integrated Windows Authentication, X. SAML2, OAuth. After successful authentication, the browser has established an authenticated user session with this trusting web application. The webapplication code loaded in the browser HTML5, Java. Script invokes HTTP GET requests to the Gateway REST services to retrieve data. The GET request can only be used to retrieve data, not to request a modifying transaction on a Gateway service. In case the client application wants to execute a transaction via Gateway REST service, it must invoke this via a POST, PUT or DELETE request. To ensure to the trusting Gateway REST service that the transaction request indeed originates from the user through the client application, the request must be signed with a CSRF Token as secret key only known by the client application context and the Gateway webapplication. The CSRF Token must be requested by the client application from the Gateway webservice. This can only be done via a non modifying HTTP GET request. If the client application needs the CSRF Token for subsequent transactional requests, it must include header variable X CSRF Token with value FETCH in a non modifying HTTP Get request send to the Gateway service. As all browsers enforce same origin policy, the browser will only send HTTP GET requests issued from resourcecode loaded in the browser that has the same origindomain as the Gateway REST service. When code loaded via another cross site tries to send the HTTP GET request, the browser will refuse to send it. Gateway webservice only serves request to return X CSRF Token for non modifying HTTP GET Request. It is not possible to retrieve the X CSRF Token via a modifying HTTP PUTPOSTDELETE action. Reason is that these requests are not subject to same origin policy, and thus can be issued from code loaded from another domain note the essence of JSONP crossdomain handling. When Gateway receives a non modifing GET Request with header variable X CSRF Token equal to FETCH, it random generates a new token and returns the generated value to the requesting client in the response via header variable and cookie. As result of same origin browser policy, cookies can only be read by javascript code originating from the same domain. Malicious code loaded from another domain cannot read the cookie nor header variable. Also the random generated value cannot reasonable be guessed by the malicious code. The client application reads the CSRF Token from the HTTP GET Response, and includes the value as header parameter X CSRF Token in modifying HTTP requests to Gateway webservice. As the token value is also returned in GET FETCH response via cookie, the value will also be included as cookie variable in each subsequent request from the client application in the current browser session. When Gateway receives a modifying request, SAP ICF runtime inspects the request on presence of X CSRF Token in both request header as in cookie.
Gateway protection against Cross Site Request Forgery attacks. Gateway REST services open up the SAP landscape for consumption and operation from clients outside that trusted SAP landscape, including those evil browsers. Evil as we all know, the web cannot be trusted. A critical aspect in the Gateway architecture is therefore to mitigate the impact of web based security attacks. Cross Site Request Forgery CSRFOne of the most exploited security vulnerabilities on the web is cross site request forgery. The essence of a CSRF attack is that a malicious site misleads a trusting site in believing that a transactional request comes with approval of the user. The working of a CSRF attack is as follows 1 after the user has set up an authenticated session with an application site, 2 the user while still within this authenticated browser session visits a malicious site, and 3 the malicious site tricks the user in sending requests to the application site that are actually constructed by the malicious site. Misleading the trusting site that the request comes with approval from the authenticated and authorized user, while in fact it originates from a malicious site. Hence the name cross site request forgery. The success of CSRF attacks depends on 3 factors The ability to load malicious javascript code within the authenticated browser session. The ability to misuse the user authentication to the application site. In most browserwebapplications scenarios the users authentication state is maintained in cookies after successful authentication required to preserve the authenticated state. If the malicious site can lure the user into sending a malicious request from the authenticated browser session, that request will automatically include all cookies including the authentication state. And thus be authorized to the trusting site without the user being aware nor approved the request. The predictability of the transaction request, so that the malicious site is able to automatically construct a request that will be serviced by the trusting site. The first factor is common exploited by social engineering. The user is somehow seduced to load javascript code from the malicious site into the current browser session, without the user even be aware. Typical example is to send an email to user with hidden javascript code, and when the user opens it a request is send to malicious site. The protection against this risk are a combination of tooling mail filters and educating the users do not just open any received mail. Although the quality of both security measures increases yes, users are also more and more aware of the risks on the web, this protection is certainly yet not 1. Note that this factor is only present if the consumption of the webservices is via a browser. In case of a native application, and also in case of an embedded browser in native App e. Fiori Client, Kapsel, Cordova, the user cannot visit others sites and have its client context become infected compromised. The second factor is inherent present in all browsers. Without it, each request send from browser would first need to go through the authentication protocol with the remote webapplication, involving browser redirects, identity stores. And in case of usernamepassword browser logon, the user would have to reenter hisher credentials over and over again. Thus preserving the authentication state after initial authentication is needed to avoid the processing and elapse time for the authentication protocol handling, and to prevent unhappy users. User friendliness and security are often in contradiction. Protection against CSRF attacks CSRF Token. CSRF protection focusses on the 3rd factor make sure the request cannot be automically predicted and thus constructed. Introduce CSRF Token protection. Blackberry Os 10 Download For Playbook Bar more. The essence of CSRF Token protection is that the token is a secret key that is only known to the authenticated browser session and the trusting site, and that the authenticated browser session must include in each modifying request to the trusting site in order to convince the trusting site that the request is coming with consent from the user. CSRF token protection is utilized on modern webapplication platforms, including SAP ICF, Microsoft IIS, CSRF protection applied in Gateway. SAP Gateway applies the following protocol to protect against CSRF The user opens in browser a session with the Gateway based webapplication, and must first authenticate. This can be via any of the authentication methods usernamepassword, integrated Windows Authentication, X. SAML2, OAuth. After successful authentication, the browser has established an authenticated user session with this trusting web application. The webapplication code loaded in the browser HTML5, Java. Script invokes HTTP GET requests to the Gateway REST services to retrieve data. The GET request can only be used to retrieve data, not to request a modifying transaction on a Gateway service. In case the client application wants to execute a transaction via Gateway REST service, it must invoke this via a POST, PUT or DELETE request. To ensure to the trusting Gateway REST service that the transaction request indeed originates from the user through the client application, the request must be signed with a CSRF Token as secret key only known by the client application context and the Gateway webapplication. The CSRF Token must be requested by the client application from the Gateway webservice. This can only be done via a non modifying HTTP GET request. If the client application needs the CSRF Token for subsequent transactional requests, it must include header variable X CSRF Token with value FETCH in a non modifying HTTP Get request send to the Gateway service. As all browsers enforce same origin policy, the browser will only send HTTP GET requests issued from resourcecode loaded in the browser that has the same origindomain as the Gateway REST service. When code loaded via another cross site tries to send the HTTP GET request, the browser will refuse to send it. Gateway webservice only serves request to return X CSRF Token for non modifying HTTP GET Request. It is not possible to retrieve the X CSRF Token via a modifying HTTP PUTPOSTDELETE action. Reason is that these requests are not subject to same origin policy, and thus can be issued from code loaded from another domain note the essence of JSONP crossdomain handling. When Gateway receives a non modifing GET Request with header variable X CSRF Token equal to FETCH, it random generates a new token and returns the generated value to the requesting client in the response via header variable and cookie. As result of same origin browser policy, cookies can only be read by javascript code originating from the same domain. Malicious code loaded from another domain cannot read the cookie nor header variable. Also the random generated value cannot reasonable be guessed by the malicious code. The client application reads the CSRF Token from the HTTP GET Response, and includes the value as header parameter X CSRF Token in modifying HTTP requests to Gateway webservice. As the token value is also returned in GET FETCH response via cookie, the value will also be included as cookie variable in each subsequent request from the client application in the current browser session. When Gateway receives a modifying request, SAP ICF runtime inspects the request on presence of X CSRF Token in both request header as in cookie.