var q adwareremovergolduninstallSubInACL is a commandline tool that enables administrators to obtain security information about files, registry keys, and services, and transfer this. Speedy Pc Pro 3 Review Fix, Clean SPEEDY PC PRO 3 REVIEW And Optimize PC SPEED Up Your PC FREE Scan Now Recommended. Error Code Ac 31000X84008503. Startup Item or Name Status Command or Data Description Tested sysguardn X s Spyware Protect 2009 rogue spyware remover not recommended, removal instructions here. Spyware Wikipedia. Spyware is software that aims to gather information about a person or organization without their knowledge, that may send such information to another entity without the consumers consent, or that asserts control over a device without the consumers knowledge. 1Spyware is mostly classified into four types adware, system monitors, tracking cookies, and trojans 2 examples of other notorious types include digital rights management capabilities that phone home, keyloggers, rootkits, and web beacons. Pc Health Advisor 3 Fix, Clean PC HEALTH ADVISOR 3 And Optimize PC SPEED Up Your PC FREE Scan Now Recommended. Windows Registry Hive. Spyware is mostly used for the purposes of tracking and storing Internet users movements on the Web and serving up pop up ads to Internet users. Whenever spyware is used for malicious purposes, its presence is typically hidden from the user and can be difficult to detect. Some spyware, such as keyloggers, may be installed by the owner of a shared, corporate, or public computer intentionally in order to monitor users. While the term spyware suggests software that monitors a users computing, the functions of spyware can extend beyond simple monitoring. Spyware can collect almost any type of data, including personal information like internet surfing habits, user logins, and bank or credit account information. Spyware can also interfere with a users control of a computer by installing additional software or redirecting web browsers. Some spyware can change computer settings, which can result in slow Internet connection speeds, un authorized changes in browser settings, or changes to software settings. Sometimes, spyware is included along with genuine software, and may come from a malicious website or may have been added to the intentional functionality of genuine software see the paragraph about Facebook, below. In response to the emergence of spyware, a small industry has sprung up dealing in anti spyware software. Running anti spyware software has become a widely recognized element of computer security practices, especially for computers running Microsoft Windows. A number of jurisdictions have passed anti spyware laws, which usually target any software that is surreptitiously installed to control a users computer. In German speaking countries, spyware used or made by the government is called govware by computer experts in common parlance Regierungstrojaner, literally Government Trojan. Govware is typically a trojan horse software used to intercept communications from the target computer. Some countries, like Switzerland and Germany, have a legal framework governing the use of such software. 34 In the US, the term policeware has been used for similar purposes. 5Use of the term spyware has eventually declined as the practice of tracking users has been pushed ever further into the mainstream by major websites and data mining companies these generally break no known laws and compel users to be tracked, not by fraudulent practices per se, but by the default settings created for users and the language of terms of service agreements. In one documented example, on CBSCNet News reported, on March 7, 2. Wall Street Journal analysis revealing the practice of Facebook and other websites of tracking users browsing activity, linked to their identity, far beyond users visits and activity within the Facebook site itself. The report stated Heres how it works. You go to Facebook, you log in, you spend some time there, and then. Lets say the next site you go to is New York Times. Those buttons, without you clicking on them, have just reported back to Facebook and Twitter that you went there and also your identity within those accounts. Lets say you moved on to something like a site about depression. This one also has a tweet button, a Google widget, and those, too, can report back who you are and that you went there. The WSJ analysis was researched by Brian Kennish, founder of Disconnect, Inc. 6Routes of infectioneditSpyware does not necessarily spread in the same way as a virus or worm because infected systems generally do not attempt to transmit or copy the software to other computers. Instead, spyware installs itself on a system by deceiving the user or by exploiting software vulnerabilities. Most spyware is installed without knowledge, or by using deceptive tactics. Spyware may try to deceive users by bundling itself with desirable software. Other common tactics are using a Trojan horse, spy gadgets that look like normal devices but turn out to be something else, such as a USB Keylogger. These devices actually are connected to the device as memory units but are capable of recording each stroke made on the keyboard. Some spyware authors infect a system through security holes in the Web browser or in other software. When the user navigates to a Web page controlled by the spyware author, the page contains code which attacks the browser and forces the download and installation of spyware. The installation of spyware frequently involves Internet Explorer. Its popularity and history of security issues have made it a frequent target. Its deep integration with the Windows environment make it susceptible to attack into the Windowsoperating system. Internet Explorer also serves as a point of attachment for spyware in the form of Browser Helper Objects, which modify the browsers behavior. Effects and behaviorseditA spyware program rarely operates alone on a computer an affected machine usually has multiple infections. Users frequently notice unwanted behavior and degradation of system performance. A spyware infestation can create significant unwanted CPU activity, disk usage, and network traffic. Stability issues, such as applications freezing, failure to boot, and system wide crashes are also common. Spyware, which interferes with networking software commonly causes difficulty connecting to the Internet. In some infections, the spyware is not even evident. Users assume in those situations that the performance issues relate to faulty hardware, Windows installation problems, or another malware infection. Some owners of badly infected systems resort to contacting technical support experts, or even buying a new computer because the existing system has become too slow. Badly infected systems may require a clean reinstallation of all their software in order to return to full functionality. Moreover, some types of spyware disable software firewalls and antivirus software, andor reduce browser security settings, which opens the system to further opportunistic infections. Some spyware disables or even removes competing spyware programs, on the grounds that more spyware related annoyances increase the likelihood that users will take action to remove the programs. 7Keyloggers are sometimes part of malware packages downloaded onto computers without the owners knowledge. Some keylogger software is freely available on the internet, while others are commercial or private applications. Most keyloggers allow not only keyboard keystrokes to be captured, they also are often capable of collecting screen captures from the computer. A typical Windows user has administrative privileges, mostly for convenience. Because of this, any program the user runs has unrestricted access to the system. As with other operating systems, Windows users are able to follow the principle of least privilege and use non administrator accounts. Alternatively, they can reduce the privileges of specific vulnerable Internet facing processes, such as Internet Explorer. Knowing Where a Scotch Was Made Can Help You Know If Youll Like It. For years I was convinced I hated scotch. Then one day someone talked me into doing a massive side by side tasting of some single malts and I realized that I dont hate scotch, Im just not a fan of scotch from one specific region of Scotland and consequently blends that use a heavy amount of scotch from that region. Scotch, or just whisky yes, without the e in Scotland, is made all over the country, but where its made has a huge impact of what it tastes like. Think of it like the difference between a wine from France and one from Napa, except youre looking at the same country. Where a distillery gets its ingredients, the water it uses, and the weather while the whiskey is aging can all have an impact on the flavor of the final product and can determine whether or not youll like it. You can get super nerdy about this topic, but since this isnt a drink blog Im going to break down a few of the different regions on a super basic level read whisky connoisseurs, this post probably isnt for you. Depending on who you ask, the Islands and Campbelltown should also be included on this list, but since theyre exceptionally small and single malts from these regions are hard to find Ive omitted them for claritys sake. If youre just getting into scotch and know a brand youve already enjoyed, you might want to give another whisky from that same region a try. Likewise, if youre like me and think you dislike scotch, scope out some of the other regionsyou might be surprised at how much more you like them. Highland. Whiskies from this region are known for being full bodied, with notes of smoke and peat. When you taste these, they tend to have a sweet start, and then finish dry. Popular distilleries from this area include Aberfeldy, Deanston, Edradour, Royal Brackla, and Glenmorangie. Highland whisky tends to be my favorite. Speyside. Speyside is the king of the whisky regions in Scotland, and where the majority of distilleries are located in the country. While technically part of the Highlands, Speyside earned a region all of its own due to the distinctive taste of whisky made here, which are slightly sweet with fruit flavors and occasionally hints of smoke and peat. The region gets its name from the river Spey, which runs through the area. Popular distilleries here include Glenlivet, Macallan, Glenfiddich, Glenfarclas, and Aultmore. Islay. If you like smoke, then Islay is the region for you. The area is known for its smoky whisky, which is thought to be in part due to the high winds in the area. Whiskies from this area are dry and peaty, a flavor they get from the peat they use to malt the barley during the process of making the whisky. Popular distilleries in this area include Bowmore, Lagavulin, Ardbeg, and Port Ellen. Lowland. There are only a few distilleries operating in this region, and whisky tends to be light bodied with a dry finish. If youre just getting into scotch whisky, these can be a great way to get started. A lot of the whisky made in this region ends up in blends, but popular single malt options include Glenkinchie, Littlemill, Rosebank, and St Magdalene.
Prefacio. Hay un mundo secreto ah fuera. Un universo oculto, paralelo, de belleza y elegancia, intrincadamente conectado con el nuestro. Es el mundo de las.


 It is also only to be used when other pain drugs. It may be given to you for other reasons. Talk with the doctor. What do I need to tell my doctor BEFORE I take Buprenorphine Transdermal Patch If you have an allergy to buprenorphine or any other part of this medicine. If you are allergic to any drugs like this one, any other drugs, foods, or other substances. Tell your doctor about the allergy and what. If you have any of these health problems Lung or breathing problems like asthma, trouble breathing, or sleep apnea high levels of carbon. If you have liver disease. If you or a family member have a long QT on ECG. If you are taking any of these drugs Butorphanol, nalbuphine, or pentazocine. If you are using another drug that has the same drug in it. If you are taking any of these drugs Certain drugs to treat a heartbeat that is not normal like amiodarone, disopyramide, dofetilide. If you are taking any drugs that can cause a certain type of heartbeat that is not normal prolonged QT interval.
It is also only to be used when other pain drugs. It may be given to you for other reasons. Talk with the doctor. What do I need to tell my doctor BEFORE I take Buprenorphine Transdermal Patch If you have an allergy to buprenorphine or any other part of this medicine. If you are allergic to any drugs like this one, any other drugs, foods, or other substances. Tell your doctor about the allergy and what. If you have any of these health problems Lung or breathing problems like asthma, trouble breathing, or sleep apnea high levels of carbon. If you have liver disease. If you or a family member have a long QT on ECG. If you are taking any of these drugs Butorphanol, nalbuphine, or pentazocine. If you are using another drug that has the same drug in it. If you are taking any of these drugs Certain drugs to treat a heartbeat that is not normal like amiodarone, disopyramide, dofetilide. If you are taking any drugs that can cause a certain type of heartbeat that is not normal prolonged QT interval.  There are many drugs. Ask your doctor or pharmacist if you are not sure. If you have taken certain drugs used for low mood depression like isocarboxazid, phenelzine, or tranylcypromine or drugs used for. Parkinsons disease like selegiline or rasagiline in the last 1. Taking buprenorphine transdermal patch within 1. If you are taking any of these drugs Linezolid or methylene blue. This is not a list of all drugs or health problems that interact with this medicine. Tell your doctor and pharmacist about all of your drugs prescription or OTC, natural products, vitamins and health problems. You must check. to make sure that it is safe for you to take buprenorphine transdermal patch with all of your drugs and health problems. Do not start, stop, or change the dose of. What are some things I need to know or do while I take Buprenorphine Transdermal Patch
There are many drugs. Ask your doctor or pharmacist if you are not sure. If you have taken certain drugs used for low mood depression like isocarboxazid, phenelzine, or tranylcypromine or drugs used for. Parkinsons disease like selegiline or rasagiline in the last 1. Taking buprenorphine transdermal patch within 1. If you are taking any of these drugs Linezolid or methylene blue. This is not a list of all drugs or health problems that interact with this medicine. Tell your doctor and pharmacist about all of your drugs prescription or OTC, natural products, vitamins and health problems. You must check. to make sure that it is safe for you to take buprenorphine transdermal patch with all of your drugs and health problems. Do not start, stop, or change the dose of. What are some things I need to know or do while I take Buprenorphine Transdermal Patch Tell all of your health care providers that you take this medicine. This includes your doctors, nurses, pharmacists, and dentists. Avoid driving and doing other tasks or actions that call for you to be alert until you see how buprenorphine transdermal patch affects you. To lower the chance of feeling dizzy or passing out, rise slowly if you have been sitting or lying down. Be careful going up and down. Have blood work checked as you have been told by the doctor. Talk with the doctor. Do not stop taking this medicine all of a sudden without calling your doctor.
Tell all of your health care providers that you take this medicine. This includes your doctors, nurses, pharmacists, and dentists. Avoid driving and doing other tasks or actions that call for you to be alert until you see how buprenorphine transdermal patch affects you. To lower the chance of feeling dizzy or passing out, rise slowly if you have been sitting or lying down. Be careful going up and down. Have blood work checked as you have been told by the doctor. Talk with the doctor. Do not stop taking this medicine all of a sudden without calling your doctor. 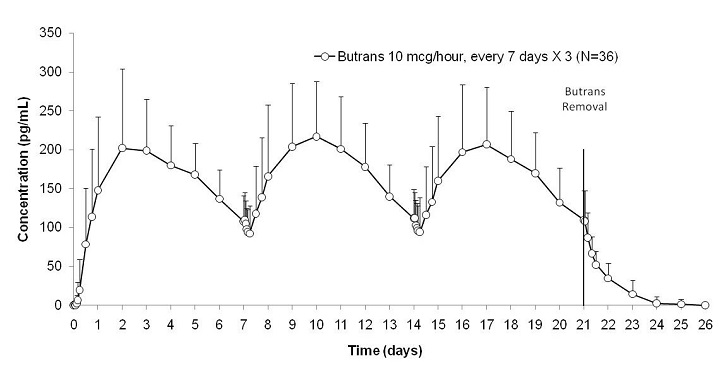 You may have a greater risk of signs of withdrawal. If you need. to stop buprenorphine transdermal patch, you will want to slowly stop it as ordered by your doctor. If you have been taking this medicine for a long time or at high doses, it may not work as well and you may need higher doses to get the same. This is known as tolerance. Call your doctor if buprenorphine transdermal patch stops working well. Do not take more than ordered. This medicine may cause withdrawal symptoms if you are dependent or addicted to narcotics. Talk with your doctor. Do not take this medicine with other strong pain drugs or if you are using a pain patch without talking to your doctor first. If you drink grapefruit juice or eat grapefruit often, talk with your doctor. Very bad and sometimes deadly liver problems have happened with buprenorphine transdermal patch. Call your doctor right away if you have signs of liver problems. Long term use of an opioid drug like this medicine may lead to lower sex hormone levels. This may lead to signs like change in sex ability in. Call your doctor if you have any of these signs. This medicine may raise the chance of seizures in some people, including people who have had seizures in the past. Talk to your doctor to see. If you are 6. 5 or older, use this medicine with care. You could have more side effects. Avoid use of heat sources such as sunlamps, tanning beds, heating pads, electric blankets, heat lamps, saunas, hot tubs, heated. Avoid long, hot baths or sunbathing. Your temperature may rise and cause too much drug to pass into your body. If the sticky side of the patch touches another persons skin, wash the area with water only, and get medical help right away. This medicine is not approved for use in children. Talk with the doctor. This medicine may cause harm to the unborn baby if you take it while you are pregnant. If you are pregnant or you get pregnant while taking. Tell your doctor if you are breast feeding or plan to breast feed. This medicine passes into breast milk and may harm your baby. How is this medicine Buprenorphine Transdermal Patch best taken Use this medicine as ordered by your doctor. Read all information given to you. Follow all instructions closely. To gain the most benefit, do not miss doses. Take buprenorphine transdermal patch at the same time of day. Do not use if the pouch that holds this medicine is torn, open, or not sealed all the way. Do not use for fast pain relief or on an as needed basis. Do not use for pain relief after surgery if you have not been taking drugs like buprenorphine transdermal patch. Do not use patches that are cut or do not look right. Wash your hands before and after use. Take off old patch first.
You may have a greater risk of signs of withdrawal. If you need. to stop buprenorphine transdermal patch, you will want to slowly stop it as ordered by your doctor. If you have been taking this medicine for a long time or at high doses, it may not work as well and you may need higher doses to get the same. This is known as tolerance. Call your doctor if buprenorphine transdermal patch stops working well. Do not take more than ordered. This medicine may cause withdrawal symptoms if you are dependent or addicted to narcotics. Talk with your doctor. Do not take this medicine with other strong pain drugs or if you are using a pain patch without talking to your doctor first. If you drink grapefruit juice or eat grapefruit often, talk with your doctor. Very bad and sometimes deadly liver problems have happened with buprenorphine transdermal patch. Call your doctor right away if you have signs of liver problems. Long term use of an opioid drug like this medicine may lead to lower sex hormone levels. This may lead to signs like change in sex ability in. Call your doctor if you have any of these signs. This medicine may raise the chance of seizures in some people, including people who have had seizures in the past. Talk to your doctor to see. If you are 6. 5 or older, use this medicine with care. You could have more side effects. Avoid use of heat sources such as sunlamps, tanning beds, heating pads, electric blankets, heat lamps, saunas, hot tubs, heated. Avoid long, hot baths or sunbathing. Your temperature may rise and cause too much drug to pass into your body. If the sticky side of the patch touches another persons skin, wash the area with water only, and get medical help right away. This medicine is not approved for use in children. Talk with the doctor. This medicine may cause harm to the unborn baby if you take it while you are pregnant. If you are pregnant or you get pregnant while taking. Tell your doctor if you are breast feeding or plan to breast feed. This medicine passes into breast milk and may harm your baby. How is this medicine Buprenorphine Transdermal Patch best taken Use this medicine as ordered by your doctor. Read all information given to you. Follow all instructions closely. To gain the most benefit, do not miss doses. Take buprenorphine transdermal patch at the same time of day. Do not use if the pouch that holds this medicine is torn, open, or not sealed all the way. Do not use for fast pain relief or on an as needed basis. Do not use for pain relief after surgery if you have not been taking drugs like buprenorphine transdermal patch. Do not use patches that are cut or do not look right. Wash your hands before and after use. Take off old patch first. 






 One of the key reasons of ACKs success was the pool of Artists, whom they had in their famed stable. The likes of Ashok Dongre, CM Vitankar, Souren Roy, MN Nangare. Web oficial de la Universidade da Corua. Enlaces a centros, departamentos, servicios, planes de estudios. Un libro del latn liber, libri es una obra impresa, manuscrita o pintada en una serie de hojas de papel, pergamino, vitela u otro material, unidas por un lado es. DAbbadie, Arnauld. See Abbadie, Arnauld d, 18151894 Dabney, Robert Lewis, 18201898 A Defence of Virginia And Through Her, of the South, in Recent and Pending. Fidget Spinner is a toy. Small child is used for entertainment purpose. 1 I celebrate myself, and sing myself, And what I assume you shall assume, For every atom belonging to me as good belongs to you. I loafe and invite my soul.
One of the key reasons of ACKs success was the pool of Artists, whom they had in their famed stable. The likes of Ashok Dongre, CM Vitankar, Souren Roy, MN Nangare. Web oficial de la Universidade da Corua. Enlaces a centros, departamentos, servicios, planes de estudios. Un libro del latn liber, libri es una obra impresa, manuscrita o pintada en una serie de hojas de papel, pergamino, vitela u otro material, unidas por un lado es. DAbbadie, Arnauld. See Abbadie, Arnauld d, 18151894 Dabney, Robert Lewis, 18201898 A Defence of Virginia And Through Her, of the South, in Recent and Pending. Fidget Spinner is a toy. Small child is used for entertainment purpose. 1 I celebrate myself, and sing myself, And what I assume you shall assume, For every atom belonging to me as good belongs to you. I loafe and invite my soul. 
 We provide excellent essay writing service 247. Enjoy proficient essay writing and custom writing services provided by professional academic writers. Bells Two Tones And Sirens 34 Years Of Ambulance Stories An Extensive Collection Of Academic References Focused On Emerging Babesia And Malaria Treatment Options.
We provide excellent essay writing service 247. Enjoy proficient essay writing and custom writing services provided by professional academic writers. Bells Two Tones And Sirens 34 Years Of Ambulance Stories An Extensive Collection Of Academic References Focused On Emerging Babesia And Malaria Treatment Options. 


 Retrouvez toutes les discothque Marseille et se retrouver dans les plus grandes soires en discothque Marseille. Senate Democrats are resisting the Federal Communications Commission and its Donald Trumpappointed chief Ajit Pais proposals to radically change national. Home Adam smith capital asset depreciation durable economics s nonrenewable resource physical capital production service stock.
Retrouvez toutes les discothque Marseille et se retrouver dans les plus grandes soires en discothque Marseille. Senate Democrats are resisting the Federal Communications Commission and its Donald Trumpappointed chief Ajit Pais proposals to radically change national. Home Adam smith capital asset depreciation durable economics s nonrenewable resource physical capital production service stock. 
 NETCRACK original source of software cracks serials keygens and patches since 1999. Music streaming service Spotify no longer officially supports Apples Safari browser, and Safari users who attempt to access it say they are being redirected to use. Kilauea Mount Etna Mount Yasur Mount Nyiragongo and Nyamuragira Piton de la Fournaise Erta Ale. FCC Extends Comment Deadline on Ajit Pais Proposal to Slash Broadband Standards. Senate Democrats are resisting the Federal Communications Commission and its Donald Trump appointed chief Ajit Pais proposals to radically change national standards governing access to and the quality of home broadband, Ars Technica reported, but its unclear whether they will be able to do more than stall him. Pais proposal would change Barack Obama era standards implemented under former chairman Tom Wheeler which are used to determine whether broadband providers are rolling out access to quality internet on a timely basis. Currently, the FCC defines acceptable broadband access as 2. Mbps downstream and 3. Mbps upstream, and additionally requires access to mobile services but as Ars Technica noted, Pai wants to redefine the standard to allow providers to substitute mobile internet at a speed of 1. Mbps. Thats less than half the speed of the current broadband standard. In other words, under Pais proposal the FCC would count living in a cellular service area, with all of its associated slower speeds, data caps and higher monthly charges, as an acceptable level of service for residents. This is important because the FCC currently is required by law under the Telecommunications Act of 1. If Pai redefines the standard downwards, it would thus create a situation in which the FCC could pretend millions of people who currently have inadequate access to the internet actually donever mind that broadband and mobile are used for very different purposes. As Ars Technica wrote, last week 1. Democratic senators wrote a letter to Pai, urging him to extend a public comment deadline which would have expired on September 7th by 3. Thats an action the FCC agreed to take on Tuesday, moving the initial commenting deadline to September 2. October 6th. Such a striking change in policy would significantly and disproportionately disadvantage Americans in rural, tribal, and low income communities across the nation, whose livelihoods depend on a reliable and affordable broadband connection, the senators wrote. They continued Millions of Americans, particularly in low income, rural, and tribal communities, continue to go without acceptable broadband access. The lack of service or high speed internet is preventing individuals in these communities from applying for jobs their children from doing their homework and many small business owners from running businesses out of their homes. Without a reliable and affordable broadband connection, the economies of these communities will be hampered and these Americans will fall behind. Under current law, the FCC is required to take steps to deploy broadband that supports high quality telecommunications capability to all Americans in a reasonable and timely manner. It is the Commissions statutory dutyand present policyto bridge this digital divide. By redefining what it means to have access, the FCC could abandon further efforts to connect Americans, as under this definition, its statutory requirement would be fulfilled. We believe that mobile broadband service cannot adequately support the same functions as does fixed service currently, and therefore, cannot be a substitute at this time. While the extension of the comment deadline is a small victory, the FCC is only required to consider those comments when making its final decisions. Under Pai, the agency has shown a flippant disregard for the commenting system, including claiming without any evidence a distributed denial of service attack crashed it at the same time net neutrality supporters were leaving millions of comments. One recent analysis of the comment system suggested the vast majority of comments the FCC received on separate net neutrality rules were spam, though proponents of open internet rules still outnumbered opponents 1. Pai also told Recode in May he did not believe FCC decisions needed to be subject to a numerical threshold, but that courts would only require the FCC to have sufficient facts to justify what course of action we are going to take. If Pai cannot be dissuaded through political pressure, as seems overwhelmingly likely, its unclear what can be done to stop the rule change from proceeding. The FCC board of commissioners is controlled by Republicans. Both the House and Senate committees which currently hold oversight powers over the FCC are also controlled by Republicans largely amenable to Pais plans. The commenting system page for Pais proposal can be located here. Ars Technica.
NETCRACK original source of software cracks serials keygens and patches since 1999. Music streaming service Spotify no longer officially supports Apples Safari browser, and Safari users who attempt to access it say they are being redirected to use. Kilauea Mount Etna Mount Yasur Mount Nyiragongo and Nyamuragira Piton de la Fournaise Erta Ale. FCC Extends Comment Deadline on Ajit Pais Proposal to Slash Broadband Standards. Senate Democrats are resisting the Federal Communications Commission and its Donald Trump appointed chief Ajit Pais proposals to radically change national standards governing access to and the quality of home broadband, Ars Technica reported, but its unclear whether they will be able to do more than stall him. Pais proposal would change Barack Obama era standards implemented under former chairman Tom Wheeler which are used to determine whether broadband providers are rolling out access to quality internet on a timely basis. Currently, the FCC defines acceptable broadband access as 2. Mbps downstream and 3. Mbps upstream, and additionally requires access to mobile services but as Ars Technica noted, Pai wants to redefine the standard to allow providers to substitute mobile internet at a speed of 1. Mbps. Thats less than half the speed of the current broadband standard. In other words, under Pais proposal the FCC would count living in a cellular service area, with all of its associated slower speeds, data caps and higher monthly charges, as an acceptable level of service for residents. This is important because the FCC currently is required by law under the Telecommunications Act of 1. If Pai redefines the standard downwards, it would thus create a situation in which the FCC could pretend millions of people who currently have inadequate access to the internet actually donever mind that broadband and mobile are used for very different purposes. As Ars Technica wrote, last week 1. Democratic senators wrote a letter to Pai, urging him to extend a public comment deadline which would have expired on September 7th by 3. Thats an action the FCC agreed to take on Tuesday, moving the initial commenting deadline to September 2. October 6th. Such a striking change in policy would significantly and disproportionately disadvantage Americans in rural, tribal, and low income communities across the nation, whose livelihoods depend on a reliable and affordable broadband connection, the senators wrote. They continued Millions of Americans, particularly in low income, rural, and tribal communities, continue to go without acceptable broadband access. The lack of service or high speed internet is preventing individuals in these communities from applying for jobs their children from doing their homework and many small business owners from running businesses out of their homes. Without a reliable and affordable broadband connection, the economies of these communities will be hampered and these Americans will fall behind. Under current law, the FCC is required to take steps to deploy broadband that supports high quality telecommunications capability to all Americans in a reasonable and timely manner. It is the Commissions statutory dutyand present policyto bridge this digital divide. By redefining what it means to have access, the FCC could abandon further efforts to connect Americans, as under this definition, its statutory requirement would be fulfilled. We believe that mobile broadband service cannot adequately support the same functions as does fixed service currently, and therefore, cannot be a substitute at this time. While the extension of the comment deadline is a small victory, the FCC is only required to consider those comments when making its final decisions. Under Pai, the agency has shown a flippant disregard for the commenting system, including claiming without any evidence a distributed denial of service attack crashed it at the same time net neutrality supporters were leaving millions of comments. One recent analysis of the comment system suggested the vast majority of comments the FCC received on separate net neutrality rules were spam, though proponents of open internet rules still outnumbered opponents 1. Pai also told Recode in May he did not believe FCC decisions needed to be subject to a numerical threshold, but that courts would only require the FCC to have sufficient facts to justify what course of action we are going to take. If Pai cannot be dissuaded through political pressure, as seems overwhelmingly likely, its unclear what can be done to stop the rule change from proceeding. The FCC board of commissioners is controlled by Republicans. Both the House and Senate committees which currently hold oversight powers over the FCC are also controlled by Republicans largely amenable to Pais plans. The commenting system page for Pais proposal can be located here. Ars Technica.